
Privileged Access Management (PAM) is essential due to its role in securing, controlling, and monitoring access to your most critical systems and sensitive data. By enforcing the principle of least privilege, PAM greatly reduces the risk of data breaches, many of which involve the misuse of privileged access. This system also guarantees regulatory compliance through detailed audit trails and monitoring. Automated provisioning, session recording, and continuous oversight enhance security and minimize human error. Implementing PAM not only safeguards against cyber threats but also mitigates insider risks, bolstering your overall cybersecurity posture. Discover more about how PAM can transform your security strategy.
Understanding Privileged Access Management (PAM)
To comprehend Privileged Access Management (PAM), you’ll need to grasp its definition, key components, and functionalities.
PAM refers to the methods and technologies used to secure, control, and monitor access to an organization’s critical systems and sensitive data. Key components of PAM systems include privileged user account management, session monitoring, and secure credential storage, all of which work together to enhance security and guarantee compliance.
Definition of Privileged Access Management
Privileged Access Management (PAM) focuses on controlling and monitoring who’s access to an organization’s most sensitive data and critical systems. At its core, privileged access management guarantees that only authorized users can perform privileged activities, minimizing the risk of data breaches and unauthorized access.
By implementing PAM, you can enforce the principle of least privilege, granting users only the permissions necessary to perform their job functions. This reduces the attack surface and mitigates the risk of insider threats.
Effective access control is essential in managing privileged accounts, which are often targeted by cybercriminals. With PAM, you can secure these accounts by storing administrative credentials in highly secure password vaults, ensuring they’re accessed only when necessary.
Additionally, PAM solutions offer thorough tracking and auditing of all privileged activities, allowing for greater visibility into user actions and helping to ensure compliance with regulatory requirements.
Key Components of PAM Systems
PAM systems, essential for safeguarding critical data, consist of three key components: Privileged Account Management (PAM), Privileged Session Management (PSM), and Privileged Elevation and Delegation Management (PEDM). Privileged Account Management involves securing, managing, and auditing privileged accounts and credentials. This component guarantees that only authorized users have access to critical systems, reducing the risk of data breaches.
Privileged Session Management focuses on monitoring and recording activities during privileged sessions, providing detailed control and extensive reports. This guarantees that all actions are tracked, which is crucial for audits and compliance.
Privileged Elevation and Delegation Management allows you to grant elevated access only when necessary, adhering to the principle of least privilege. This minimizes the risk of misuse by limiting the duration and scope of elevated access.
Here’s a breakdown of these components:
| Component | Description |
| Privileged Account Management | Secures and audits privileged accounts and credentials |
| Privileged Session Management | Monitors and records privileged session activities |
| Privileged Elevation and Delegation Management | Grants temporary elevated access based on necessity |
| Granular Control | Provides detailed control over privileged access |
| Detailed Reports | Generates detailed activity logs for compliance and audits |
Functionalities and Features of PAM
Incorporating robust functionalities and features, Privileged Access Management (PAM) solutions ensure that sensitive information remains secure while enhancing compliance and operational efficiency. One of the core principles PAM enforces is the principle of least privilege, ensuring users only access what’s necessary for their job functions. This minimizes the risk of unauthorized access and potential data breaches.
PAM solutions come packed with various functionalities designed to safeguard critical systems:
- Password vaulting: Securely stores and manages privileged account credentials, preventing unauthorized access.
- Audit trails: Provides detailed records of privileged access, ensuring accountability and transparency for compliance purposes.
- Automated provisioning: Streamlines user management processes by automatically granting and revoking access rights based on predefined policies.
These features are essential for tracking user activities, detecting unauthorized actions, and maintaining a high security posture.
For instance, session recording and monitoring within PAM allow organizations to review and analyze privileged user activities, adding another layer of security. Additionally, automated provisioning and deprovisioning of access rights facilitate efficient and secure user management, reducing the administrative burden and potential for human error.
The Growing Threat of Cyber Attacks on Privileged Accounts

You can’t ignore the alarming statistics and trends indicating that cyber attacks on privileged accounts are increasing at a staggering rate, with 100% of cyber attacks targeting these accounts.
High-profile breaches, often resulting from compromised access, highlight the significant impact on organizations.
As cyber criminals continuously evolve their tactics, it’s essential to understand the future threats and emerging strategies they might employ.
Statistics and Trends in Cyber Attacks
The growing threat of cyber attacks on privileged accounts underscores the urgent need for robust cyber security measures. With 74% of data breaches involving privileged access misuse, it’s clear that securing these accounts is critical. Insider threats, which 65% of organizations find harder to detect and prevent than external attacks, further highlight the necessity for stringent controls over privileged access.
Consider the following alarming facts:
- 80% of cybersecurity breaches are due to weak or stolen passwords, making privileged credentials particularly vulnerable.
- The average data breach cost involving privileged credentials is $4.52 million, emphasizing the financial impact of security lapses.
- By 2023, 75% of security failures will stem from inadequate management of identities, access, and privileges.
These statistics reveal significant trends and underscore the importance of addressing insider threats and weak passwords to prevent security failures.
Implementing Privileged Access Management (PAM) is a proactive approach to mitigating risks associated with privileged access misuse. By doing so, organizations can better protect their sensitive information, reduce the risk of costly data breaches, and safeguard against potential insider threats.
Effective PAM strategies are essential in today’s cyber landscape to maintain organizational integrity and security.
High-Profile Breaches Due to Compromised Access
When cybercriminals target privileged accounts, they exploit the extensive access rights these accounts hold, leading to devastating breaches such as the Equifax hack. Privileged access typically grants users control over critical systems and sensitive data, making them prime targets for attackers.
The Equifax breach, for instance, resulted in the exposure of personal information of over 147 million individuals, underscoring the catastrophic potential of compromised access.
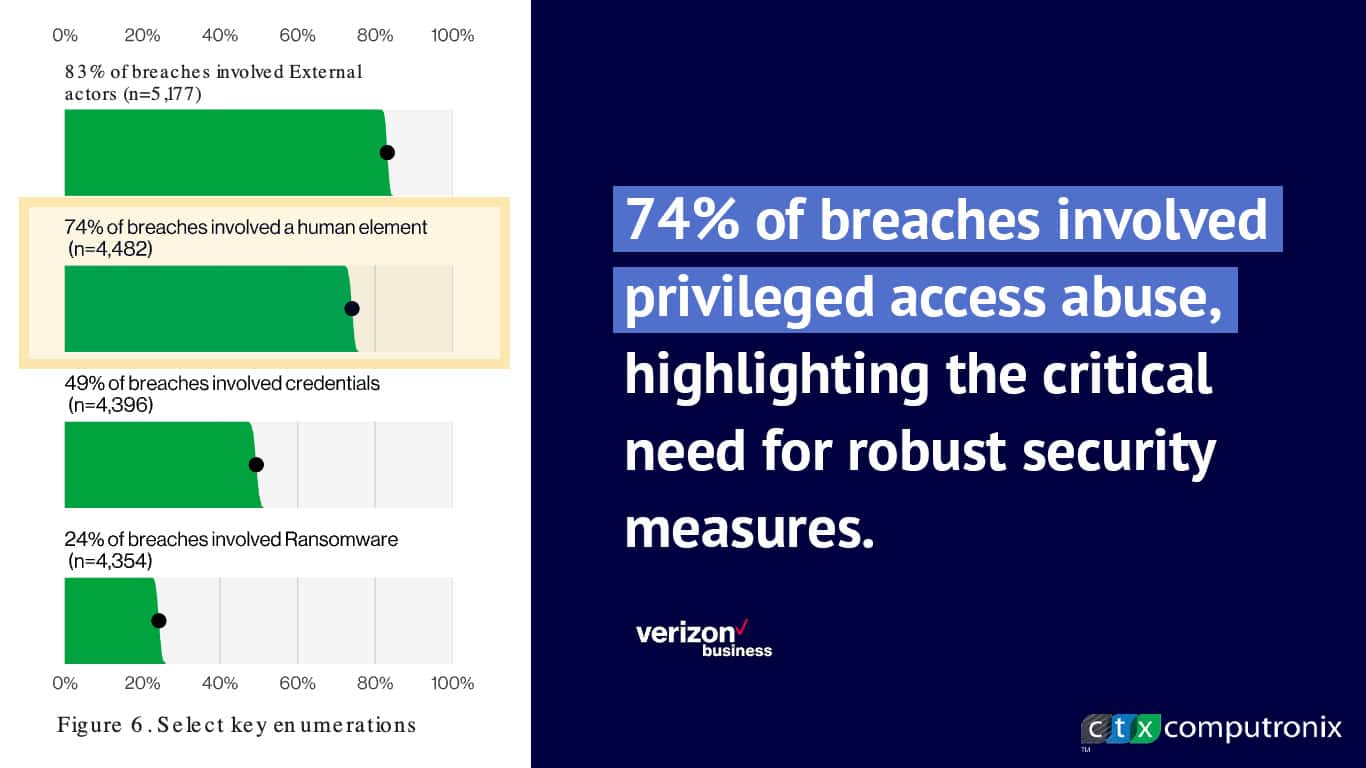
High-profile breaches often involve the abuse of privileged credentials. According to the Verizon Data Breach Investigations Report, 74% of breaches involved privileged access abuse, highlighting the critical need for robust security measures.
When privileged credentials are compromised, cybercriminals can navigate an organization’s network almost unimpeded, accessing vital data and causing substantial financial and reputational damage.
Compromised access to privileged accounts can have far-reaching consequences. Over 80% of data breaches involve these highly sensitive accounts, emphasizing the necessity of stringent privileged access management. Without adequate protection, organizations risk not only financial loss and reputational harm but also regulatory penalties.
Securing privileged accounts through thorough access management strategies is essential to safeguard your organization’s most valuable assets.
Future Threats and Emerging Tactics
Increasing cyber threats and sophisticated tactics are making privileged accounts prime targets for attackers. As these threats evolve, it’s essential to understand the future threats and emerging tactics that target privileged credentials. Cybercriminals are constantly refining their methods, and the financial impact of security breaches on privileged accounts can be devastating, with average costs reaching $4.5 million per incident.
Organizations must stay ahead of these emerging tactics to protect their privileged credentials and mitigate risks.
Attackers frequently employ:
- Phishing: Deceptive emails designed to trick users into revealing their credentials.
- Malware: Malicious software that infiltrates systems to capture sensitive information.
- Social engineering: Psychological manipulation to exploit human vulnerabilities.
These tactics highlight the need for robust security measures to safeguard privileged accounts.
With 74% of organizations experiencing breaches due to compromised privileged access, the importance of Privileged Access Management (PAM) can’t be overstated. Effective PAM solutions help reduce the risk of future threats by controlling and monitoring access to critical systems and data.
As the threat landscape continues to grow, implementing PAM is essential for maintaining the integrity and security of your organization’s assets.
Protecting Sensitive Data with Privileged Access Management
To protect sensitive data, you must secure privileged accounts by enforcing strict access controls and monitoring activities, which is the cornerstone of Privileged Access Management (PAM).
Preventing unauthorized access is crucial, as it not only mitigates risks of insider threats and cyber attacks but also guarantees compliance with regulatory requirements.
Importance of Securing Privileged Accounts
Securing privileged accounts is essential for protecting sensitive data from unauthorized access and ensuring the integrity of critical systems. Privileged access management (PAM) plays a pivotal role in safeguarding your organization’s most valuable information. By effectively managing privileged accounts, you’re not only protecting sensitive data but also fulfilling critical compliance requirements.
Privileged accounts, with their broad-reaching powers, are prime targets for cyberattacks. Without proper control, these accounts can be exploited, leading to significant data breaches. Implementing a robust PAM solution mitigates these risks by enforcing the principle of least privilege, ensuring users only have access to the information they need to perform their duties. This approach helps in:
- Enhancing security: Limiting access reduces the attack surface, making it harder for malicious actors to infiltrate critical systems.
- Ensuring compliance: Detailed audit trails of privileged activities help meet regulatory standards and avoid costly penalties.
- Increasing visibility: Monitoring and logging user activities provide insights into potential security threats and unauthorized access attempts.
Preventing Unauthorized Access
Achieving unauthorized access to sensitive data becomes attainable by implementing Privileged Access Management (PAM) systems that restrict elevated permissions to only those who genuinely need them. By doing so, you greatly decrease the risk of data breaches and limit exposure to insider threats. PAM guarantees that only authorized personnel can access critical systems and information, thereby enhancing your overall security posture.
PAM systems work by controlling and monitoring privileged accounts, which helps you comply with regulatory requirements for data protection. These systems provide a detailed log of user activities, making it easier to detect and respond to any suspicious behavior. By securing administrative credentials in highly secure password vaults, you further lessen the risk of unauthorized access.
By implementing PAM, you not only protect sensitive data but also safeguard against cyber attacks targeting high-impact assets within your organization. Here’s a brief comparison to help visualize the benefits:
| Feature | Benefit |
| Restricts elevated permissions | Reduces risk of data breaches |
| Controls and monitors accounts | Enhances compliance with regulations |
| Secures administrative credentials | Mitigates insider threats |
Case Studies of Data Protection through PAM
Real-world case studies illustrate how implementing PAM solutions can effectively safeguard sensitive data and prevent unauthorized access. These case studies highlight the importance of robust data protection mechanisms and the role of PAM in mitigating the risks associated with cyber attacks targeting privileged accounts.
For instance, a global financial institution faced significant challenges in managing privileged access to its critical systems. By deploying PAM solutions, they were able to secure administrative credentials in highly secure vaults, enforce least privilege principles, and monitor user activities thoroughly. This led to enhanced data protection and compliance with regulatory requirements.
Similarly, a healthcare provider implemented PAM to protect sensitive patient information. The PAM solution restricted access to only authorized personnel, reducing the risk of data breaches and ensuring the integrity of their systems.
To keep you engaged, consider these key points:
- Enhanced security: Privileged accounts are protected against unauthorized access and cyber attacks.
- Compliance: Organizations can meet stringent regulatory requirements by controlling and monitoring privileged access.
- Risk reduction: Implementing PAM reduces the likelihood of data breaches and insider threats.
These case studies underscore the effectiveness of PAM solutions in safeguarding sensitive data, demonstrating their significant role in modern cybersecurity strategies.
Ensuring Regulatory Compliance with Privileged Access Management
In order to maintain regulatory compliance, it’s crucial to understand key regulations like GDPR, HIPAA, and SOX.
Privileged Access Management (PAM) helps you meet these requirements by maintaining audit trails, enforcing least privilege policies, and centralizing account management.
Non-compliance can result in severe penalties, making PAM a critical component for safeguarding sensitive data and adhering to industry standards.
Overview of Key Regulations (GDPR, HIPAA, SOX)
Ensuring regulatory compliance with Privileged Access Management is essential for protecting sensitive data and adhering to key regulations like GDPR, HIPAA, and SOX. These regulations mandate strict access control measures to safeguard personal and organizational data, making it important for you to understand how each one impacts your business operations.
- GDPR: The General Data Protection Regulation requires stringent controls on personal data, emphasizing access control and user permissions to protect privacy. Non-compliance can result in hefty fines and legal consequences.
- HIPAA: The Health Insurance Portability and Accountability Act focuses on securing sensitive healthcare information, ensuring only authorized personnel can access patient data. This regulation demands robust access control mechanisms to prevent unauthorized access.
- SOX: The Sarbanes-Oxley Act mandates financial data protection to prevent fraud and ensure accurate reporting. Implementing strong access control measures is crucial for compliance, as it helps secure financial records and sensitive data from unauthorized access.
How PAM Helps in Compliance
By implementing Privileged Access Management (PAM), you can guarantee that your organization meets stringent regulatory compliance requirements through detailed monitoring and auditing of privileged user activities. PAM assures that your company adheres to regulations like GDPR, HIPAA, and SOX by automatically recording all privileged access. This creates thorough audit trails, which are essential for data protection and accountability.
Compliance is more straightforward with PAM because it maintains detailed logs of privileged user actions and access to sensitive data, helping you easily pass compliance audits. These logs provide the necessary evidence that your organization is following industry regulations, showing that you have taken appropriate measures to control and monitor access.
Furthermore, PAM enforces least privilege access policies, ensuring users only have the privileges absolutely necessary for their roles. This is a key requirement for regulatory compliance, as it minimizes the risk of unauthorized access to sensitive information.
Penalties for Non-Compliance
Ignoring the importance of PAM and failing to meet regulatory requirements can result in severe penalties, including massive fines and legal consequences. Non-compliance penalties aren’t just financial burdens; they can also lead to significant legal repercussions that tarnish your organization’s reputation and credibility.
Various regulations like GDPR, HIPAA, SOX, PCI DSS, and NIST mandate stringent control and monitoring of privileged access, making the implementation of PAM a necessity.
When you don’t adhere to these industry standards, the consequences can be dire:
- Fines: Regulatory bodies can impose fines up to €20 million or 4% of your annual global turnover.
- Legal Repercussions: Non-compliance can lead to lawsuits, criminal charges, and long-term legal entanglements.
- Reputation Damage: Customers and partners may lose trust, resulting in lost business opportunities.
Reducing Insider Threats with Privileged Access Management
Understanding insider threats is essential for any organization, as these threats can be just as damaging as external attacks.
By implementing effective Privileged Access Management (PAM) strategies, you can greatly reduce the risks associated with insider threats, ensuring that sensitive data and systems are protected from unauthorized access.
Real-world examples of insider threats highlight the importance of robust PAM solutions in preventing malicious activities and safeguarding your organization’s assets.
Understanding Insider Threats
Insider threats, responsible for 34% of data breaches, pose a significant risk to organizations, but you can mitigate these risks effectively with Privileged Access Management (PAM).
Insider threats, whether malicious or accidental, often involve employees or contractors who’ve legitimate access to sensitive data and systems. By implementing PAM, you can take several steps to reduce these risks.
Firstly, PAM limits access to sensitive data, ensuring that only authorized individuals can reach critical systems. This minimizes the chance of misuse or unauthorized access.
Additionally, PAM allows you to monitor privileged user activities, making it easier to detect any anomalous behavior that could signify an insider threat.
Finally, PAM helps you maintain a secure environment by enforcing strict access control measures.
- Limit access to sensitive data: Only authorized users can access critical systems.
- Monitor privileged user activities: Detect anomalous behavior indicating potential insider threats.
- Enforce strict access controls: Maintain a secure environment by regulating who can access what.
PAM Strategies to Mitigate Insider Risks
To mitigate insider risks effectively, start by implementing robust PAM strategies that control and monitor privileged user access. By doing so, you can greatly reduce insider threats, which account for 34% of data breaches. Begin with enforcing least privilege policies, which guarantee that users only have access to the data and systems necessary for their roles. This minimizes the likelihood of insider misuse of privileged accounts and protects sensitive information.
Additionally, PAM solutions track and record privileged user activities, providing visibility into potential malicious insider behavior. Continuous monitoring allows you to detect anomalies and respond swiftly, thereby reducing risks before they escalate. Implementing these solutions not only helps in real-time detection but also aids in forensic analysis if an incident occurs.
Moreover, storing administrative credentials in secure, specialized password vaults enhances security by limiting unauthorized access. Regular audits and reviews of privileged access can further safeguard your critical assets.
Real-World Examples of Insider Threats
Real-world examples of insider threats highlight the importance of implementing robust privileged access management to protect sensitive data and systems. Insider threats are a significant concern, given that they account for nearly 60% of data breaches. Malicious insiders can cause substantial damage, costing companies an average of $4.5 million per year. By employing privileged access management, you can mitigate these risks effectively.
Consider these scenarios:

Disgruntled employees: A dissatisfied employee with access to privileged accounts could leak sensitive information or sabotage systems.

Negligent insiders: An employee might accidentally expose confidential data due to poor security practices, leading to breaches.

Third-party vendors: External vendors with privileged access can become insider threats if their credentials are compromised or misused.
Privileged access management solutions provide thorough security measures, including monitoring and auditing capabilities, to detect and prevent such insider threats in real-time. Implementing least privilege access controls ensures that users only have access to the information necessary for their roles, reducing the risk of unauthorized access.
Additionally, continuous monitoring and auditing help track user activities, providing visibility into potential security issues before they escalate.
Enhancing Operational Efficiency with Privileged Access Management
Implementing Privileged Access Management (PAM) can greatly enhance your organization’s operational efficiency by automating access provisioning and deprovisioning tasks, which streamlines administrative processes. By reducing the IT burden through automated PAM, you can save valuable time and resources, allowing your IT team to focus on more strategic initiatives.
Additionally, PAM improves response times and overall efficiency by ensuring that only authorized users have access to sensitive data and systems, thereby minimizing the risk of unauthorized activities.
Benefits of PAM in streamlining administrative processes
Privileged Access Management (PAM) greatly enhances operational efficiency by automating the provisioning and deprovisioning of privileged access. This automation reduces the time and effort required to manage privileged accounts, allowing administrators to focus on more strategic tasks. The benefits of privileged access management extend to streamlining administrative processes, which ultimately boosts operational efficiency.
By centralizing privileged account control, PAM provides a single point of management for all privileged access requests. This not only simplifies administrative tasks but also guarantees that access is granted based on predefined policies, minimizing the risk of unauthorized access. Automated workflows within PAM systems can handle repetitive tasks, further reducing the likelihood of human error.
Enhanced visibility: PAM centralizes logs and monitors privileged account activities, increasing transparency and accountability.
Policy enforcement: Automated workflows make sure that access controls are consistently applied, maintaining compliance with organizational policies.
Resource optimization:
Reducing IT Burden with Automated PAM
Leveraging automated PAM not only streamlines administrative processes but also greatly reduces the IT burden by automating access provisioning and deprovisioning. Automated privileged access management simplifies these tasks, making them quicker and more accurate, thereby reducing the workload on IT staff to a large extent. This not only leads to a reduction in IT burden but also enhances operational efficiency across the board.
With automated PAM, you can guarantee that access controls are consistently applied without manual intervention, minimizing the risk of human error. This automation strengthens your security posture, as it ensures that privileged access is granted and revoked promptly and accurately. In addition, automated privileged access management enables IT teams to focus on strategic initiatives, rather than getting bogged down with repetitive administrative tasks.
Here’s a quick overview to illustrate the benefits:
| Benefit | Impact on IT Team | Overall Effect |
| Automated Provisioning | Reduces manual workload | Increased efficiency |
| Enhanced Access Controls | Consistent security enforcement | Improved security posture |
| Focus on Strategic Tasks | Less time on administrative work | Greater innovation |
Improving Response Times and Efficiency
Efficient PAM solutions dramatically cut down response times and boost operational efficiency by automating access control processes. By integrating Privileged Access Management, you can swiftly provision and deprovision access for users, eliminating the delays that typically arise with manual access control tasks. This automation not only speeds up response times but also guarantees that privileged access is managed with precision and adherence to least privilege principles.
Consider the following benefits:
- Faster Response to Access Requests: Automated processes mean that access requests are handled promptly, enhancing operational efficiency.
- Streamlined Workflows: By reducing the time spent on manual tasks, your team can focus on more strategic initiatives.
- Improved Security Posture: Enforcing least privilege ensures that users have only the access they need, minimizing potential security risks.
PAM also enhances operational efficiency by offering real-time monitoring and auditing capabilities, allowing you to quickly identify and address any irregularities in access patterns. This proactive approach to access control not only optimizes your workflows but also strengthens your organization’s security framework. Ultimately, by automating privileged access tasks, you’re enabling your IT team to work more efficiently and effectively, ensuring that your systems remain secure and compliant.
Risk Management and Mitigation with Privileged Access Management

To effectively manage and mitigate risks associated with privileged access, you must first assess the potential vulnerabilities that come with elevated permissions.
Implementing robust risk mitigation strategies, such as enforcing least privilege principles and utilizing secure password vaults, can greatly enhance your security posture.
Assessing Risks Associated with Privileged Access
Given the extensive permissions granted to privileged accounts, they pose a significant risk as prime targets for cyber attacks. Privileged access management is essential in evaluating and mitigating these risks.
When you don’t have proper control over privileged accounts, it can lead to unauthorized access, data breaches, and compliance failures.
To effectively evaluate the risks associated with privileged access, consider the following:
- Visibility: Regularly monitor and audit privileged accounts to make sure that all activities are tracked and any suspicious behavior is identified promptly.
- Least Privilege Enforcement: Make certain that users have only the access they need to perform their duties, reducing the chance of misuse.
- Compliance Checks: Conduct regular compliance checks to verify that access controls align with industry regulations and standards.
Implementing Risk Mitigation Strategies
After evaluating the risks associated with privileged access, you need to implement effective risk mitigation strategies to safeguard your organization’s critical assets. Implementing privileged access management (PAM) is vital in establishing a holistic security and risk management framework. By controlling, monitoring, and auditing privileged accounts, you can greatly reduce the likelihood and impact of security breaches.
Privileged access management helps reduce insider threats and prevent unauthorized access by enforcing least privilege principles and ensuring that users have only the access necessary to perform their duties. This approach strengthens your organization’s overall security posture by increasing visibility into user activities and securing administrative credentials in highly secure password vaults.
When implementing risk mitigation strategies, focus on integrating PAM solutions that provide automated controls and real-time monitoring. This proactive stance enables your organization to identify and address vulnerabilities before they can be exploited, limiting exposure to cyber threats. Additionally, PAM ensures compliance with regulations by maintaining detailed audit trails and demonstrating that access to sensitive information is tightly controlled.
In essence, effective risk management through PAM involves a multi-faceted approach that combines stringent access controls, continuous monitoring, and thorough auditing to protect your organization’s most critical assets from potential security breaches.
Case Studies of Risk Reduction via PAM
In examining real-world applications, several companies have greatly reduced risk through the strategic implementation of Privileged Access Management (PAM). These case studies highlight how PAM controls can be instrumental in mitigating various security risks.
For instance, Company X managed to cut the risk of insider threats by 50% after integrating PAM, showcasing the effective use of privileged access management in safeguarding sensitive information.
- Company Y: By enforcing least privilege access, the company reduced unauthorized access risks by 75%, demonstrating the value of restricting user permissions to only what’s necessary.
- Organization Z: Implementing PAM led to a 60% decrease in security breaches, underlining the importance of managing privileged accounts effectively.
- Company A: Achieved an 80% reduction in data breach risks through granular control over privileged access, proving the effectiveness of detailed access management.
In addition, Company B successfully reduced the risk of credential theft and misuse by 70% through PAM, emphasizing the importance of securing administrative credentials. These examples clearly illustrate how PAM can play a critical role in risk reduction, ensuring that companies maintain robust security postures by effectively managing privileged access and implementing least privilege access principles.
Best Practices for Implementing Privileged Access Management
To effectively implement Privileged Access Management, you’ll want to start by conducting a thorough inventory of all privileged accounts to understand the scope of access within your organization.
Establishing least privilege policies is essential, as it guarantees that users only have access to the resources necessary for their roles.
Additionally, continuous monitoring and auditing of privileged accounts can help identify and address any potential security issues promptly.
Conducting a Privileged Account Inventory
Start by identifying and cataloging all privileged accounts within your IT environment to understand the full scope of access and potential security risks. This privileged account inventory is essential as it allows you to pinpoint all accounts with elevated access privileges, ensuring no account is overlooked. By doing so, you can better grasp the scope of privileged access and address any security risks associated with these accounts.
A thorough inventory also facilitates implementing proper controls and monitoring mechanisms. As you identify each account, evaluate its necessity and usage frequency to enforce least privilege access, minimizing the potential attack surface. Additionally, updating the privileged account inventory regularly maintains ongoing visibility and security, ensuring no new or altered accounts slip through the cracks.
To keep your audience engaged, consider these best practices:
- Comprehensive Cataloging: Document all privileged accounts, including service accounts, administrative accounts, and any third-party access.
- Regular Reviews: Schedule periodic reviews to update the inventory, ensuring it reflects current access needs and configurations.
- Automated Tools: Utilize automated tools to scan and monitor privileged accounts, enhancing accuracy and efficiency.
Establishing Least Privilege Policies
When you establish least privilege policies, you ensure that users only have the access they need to perform their job functions, greatly reducing security risks. Privileged access management hinges on this principle to mitigate potential threats. By implementing least privilege policies, you limit the scope of insider threats and reduce the damage that can be caused by compromised accounts.
Applying least privilege guarantees that users can’t access sensitive data or critical systems outside their responsibilities, thereby minimizing the impact of any security incidents. This approach not only enhances your organization’s security posture but also simplifies access control management. It streamlines the process of setting permissions and access levels, contributing to better operational efficiency.
Moreover, least privilege policies are essential for regulatory compliance. Adhering to these principles helps you meet various regulatory requirements by controlling access to sensitive information and maintaining detailed audit trails. Regulatory bodies often mandate strict access controls to protect data, and implementing least privilege is a proactive step in fulfilling these requirements.
Continuous Monitoring and Auditing
Continuous monitoring and auditing play a crucial role in maintaining the robustness and security of privileged access management. By implementing continuous monitoring, organizations can gain real-time visibility into privileged account activities. This allows them to swiftly detect and respond to unauthorized access attempts, thereby mitigating risks before they escalate into significant security breaches.
Effective auditing capabilities are essential for tracking user actions, changes, and access to critical systems. Regular audits not only help in identifying suspicious activities but also ensure compliance with regulatory requirements. An effective audit trail can reveal patterns of misuse or anomalies that might indicate potential threats, enabling organizations to take corrective actions promptly.
To help illustrate the importance of these practices, the following benefits can be considered:
- Real-Time Visibility: Immediate detection of unauthorized access and unusual activities.
- Regulatory Compliance: Meeting standards and laws through detailed audit trails.
- Risk Mitigation: Reducing the chances of data breaches by continuously monitoring privileged account activities.
Frequently Asked Questions
What Is the Purpose of Privileged Access Management?
You utilize Privileged Access Management to regulate who has access to sensitive systems and data. It guarantees only authorized users can access privileged accounts, monitors their activities, and helps prevent data breaches while maintaining compliance.
Why Is Privileged Identity Management Important?
Privileged identity management is essential because it helps you secure sensitive data and critical systems. You’ll reduce insider threats, guarantee compliance, and maintain detailed audit trails, ultimately strengthening your organization’s overall security and operational integrity.
What Are the Benefits of Implementing PAM?
Implementing PAM benefits you by boosting security, reducing data breach risks, and ensuring regulatory compliance. You’ll streamline access control, gain better visibility into user activities, and securely store administrative credentials in highly secure password vaults.
Which of the Following Are the Benefits of Pam?
You’ll find that implementing PAM provides several benefits. It limits access to critical systems, reduces data breach risks, guarantees regulatory compliance, streamlines access control, and increases visibility into user activities, protecting sensitive information effectively.
Final Thoughts

In today’s intricate digital landscape, Privileged Access Management (PAM) is essential for safeguarding your organization’s critical assets.
By controlling access to sensitive data, ensuring regulatory compliance, and mitigating risks, PAM stands as your first line of defense against cyber threats.
It reduces insider threats and enhances operational efficiency through secure, streamlined processes.
Implementing PAM thoroughly fortifies your cybersecurity posture, ensuring your organization remains resilient and secure in an ever-evolving threat environment. Secure your business with us here at Computronix.










